Into the Maze of Crypto Money Laundering
In the intricate world of cryptocurrency, the allure of anonymity often intersects with the shadowy realm of illicit activities, including money laundering. Unraveling the complexities of blockchain transactions is essential for law enforcement agencies and financial institutions seeking to combat financial crimes. This article delves into the methodology of identifying if a Bitcoin address is entangled in money laundering schemes, with a focus on the notorious tactic known as skimming. Through real-life investigations and practical examples, we’ll illuminate the techniques employed to track and trace suspicious transactions, shedding light on the crucial role of blockchain analysis in the fight against financial fraud.
Now let’s jump right in.
The Investigation
Our investigation started with a due diligence request for a Bitcoin (BTC) transaction affiliated with another company. The transaction showed approximately $14,000 sent from one address to another. Using a blockchain scanner revealed that the sending address was owned by the well-known Binance crypto exchange. The address itself was used for exchange customers to make funds withdrawals from their accounts (according to several comments posted by anonymous users on the blockchain scanner website). The receiver address appeared to be just a random address with no known affiliations. So we have a Binance Withdrawals address sending money to a random address that I will name.

Crypto Laundromats: how to trace money laundering in Bitcoin

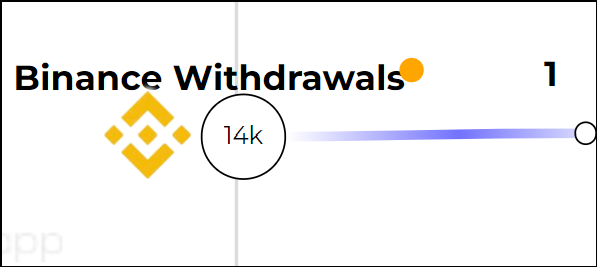
So the initial transaction was likely a withdrawal of funds, nothing interesting here. The Exchange Withdrawal address had thousands of previous transactions and by all accounts appeared innocuous. The withdrawing address (hereafter referred to as address 1) had very little activity but a few days later it made a transfer of funds to a second address (address 2), which then transferred funds to a third, and the fourth, fifth, and then sixth.

Searching all of the addresses in WalletScan reveals that address 5 was associated with ransomware.
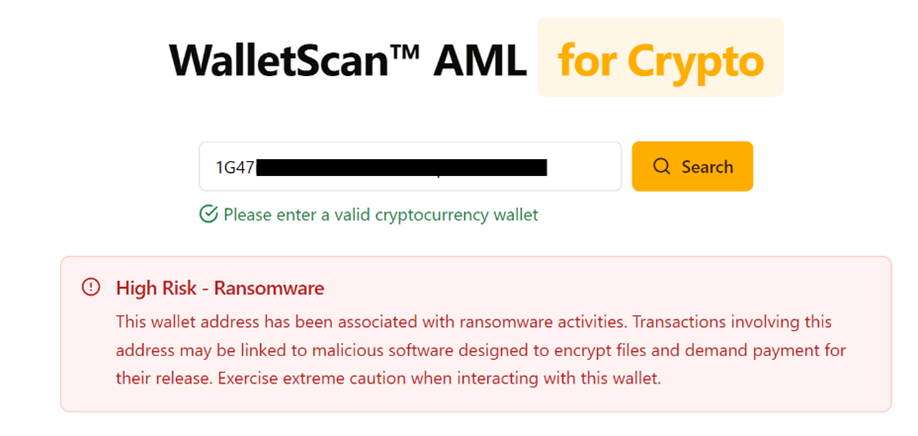
Having discovered the tentative link to the Ransomware address, we looked further into the addresses’ transaction history.
Connecting Dots: how to track crypto money-laundering

Transactions History
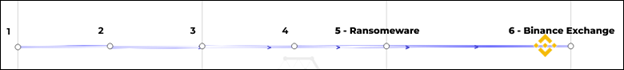
Further research into the transaction history of all addresses revealed that address 6 had thousands of previous transactions, and all transactions were inputs into the address, this is a strong indicator of it being an exchange address.
Further research in the personal comments posted on various websites showed that address 6 was owned by Binance.
So the trail of funds ends with a ransomware-affiliated address sending the funds to the Binance exchange.
Transaction Amounts
Digging further into the funds transactions, showed that:
Address 1 received $14,000 (at that time) worth of BTC and then sent $11,200 worth of BTC to address 2
Address 2 then sent $8,400 worth of BTC to address 3
Address 3 sent forward $5,600 to address 4
Address 4 sent forward $2,800 to address 5
Address 5 sent all $2,800 to address 6
Each amount is $2,800 less than the previous, meaning each address kept that same amount. This is definitely proof of a connection given the repeat behavior. So, what did each address do with the money?
UTXO?
Here let us pause for a quick backgrounder. Bitcoin has a UTXO (unspent transaction output) model, which means that an address cannot send out only part of its money, it must instead output all of its funds for every transaction.
How does this work? Let’s say you have a wallet with 10BTC and you want to buy something that costs 8 BTC. When you choose to send 8 BTC to the recipient, the other 2 BTC will go to a new third address, “change address” that is also owned by you. The change address generally sends the change back to the first address you own.
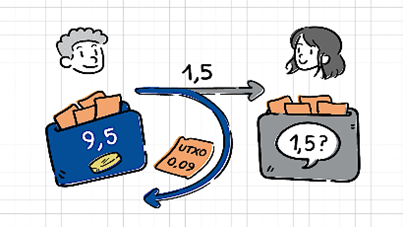
Many block scanner websites do not show the change address part of the transaction, so be aware that this happens with every BTC transaction.
Investigating Change Addresses
Block scanners showed that each address 1-5 had only had two transactions, receiving and sending the funds. Then we began digging into the transactions to look at change addresses.
And here we discovered that when Address 1 sent $11,200 to Address 2 it also sent $2,800 to a third address, which turned out to be Address 6! Similarly, address 2 sent $2,800 to address 6 and in the same transaction sent the rest to address 3. T Likewise for the other addresses each sending $2,800 to address 6 and the rest down the line.
Confusing?
Let’s visualise. We originally viewed the trail of funds as a straight line:

But we discovered the funds traveling on several lines that all ultimately went to address 6.
As soon as we see this pattern we know the money is being laundered. The flow of funds here is a classic example of “skimming”, one of the most often-used methods for laundering money.
Skimming means that the funds are sent from one account to another, owned by the same person, each address “skims” a bit from the top and sends small portions of the funds to the same final recipient. From the recipient’s perspective, they are receiving several transfers of funds from different addresses. The recipient does not see that all of these addresses are linked to each other.
How do we know that the addresses (not including the Binance address) are owned by the same person? Because each address is the change address for the previous transaction.
If address 1 sent funds to address 6 (the intended recipient) and in the same transaction sent the rest to address 2, that means that 2 was actually the changed address. Address 2 sends money to 6, and the rest goes to 3, and the pattern continues for 4 and 5. Because they were all changed addresses, that means they were all owned by the same person. So the owner of address 1 is also the owner of the Ransomeware-affiliated address 5.
Therefore, even though we don’t know the person’s identity, we see that they withdrew funds from Binance, laundered it (using a ransomware address in the process), and then sent all of the money back to Binance.
To recap, we showed how to track funds, identify money laundering activity, change addresses, and the skimming model. This example is not unique and investigators will very likely see the same features in their own investigations.
With this knowledge in hand, we must remember that as the digital landscape evolves, so too do the methods of financial criminals. This is why it is so useful to understand and appreciate advancements in blockchain analysis and new tools like Cybertrace WalletScan.
By understanding the intricacies of skimming tactics and leveraging the power of blockchain forensics, investigators will also evolve and maintain an edge over the competition.
Guest Author

About the author:
Tom Caliendo is the author of The Open Source Intelligence Guide, a book that focuses on how investigators with or without computer skills can use OSINT.
Tom is a cybersecurity journalist covering the emerging threats and Internet’s hidden layers; he is Co-Founder of the research and literary firm Brockett Consulting – brockettconsulting.com.
Tom is a lifelong investigator with a passion for educating others on the potential of OSINT. He is licensed and experienced in disparate investigative fields, including private investigation, cryptocurrency investigation, archival research, ethical hacking, and genealogy.
He lives in Virginia where he is a gardener, bee lover, and expert at chasing his five-year-old.
His book is available on Amazon –https://www.amazon.com/Open-Source-Intelligence-Guide-Anything/dp/B0C9SH1NWL
Follow Tom on his website – TheOsintGuide.com
Twitter – https://twitter.com/DeepWebOsint
Instagram – https://www.instagram.com/theosintguide_book/
Substack – https://substack.com/@theosintguide


